CrowdStrike a global cybersecurity leader, is redefining security for the cloud era with an endpoint protection platform built from the ground up to stop breaches. The CrowdStrike Falcon® platform’s single lightweight-agent architecture leverages cloud-scale artificial intelligence (AI) and offers
real-time protection and visibility across the enterprise, preventing attacks on endpoints on or off the network.
Enpoint Protection Solution
Technical Features
- Machine learning and artificial intelligence detect known and unknown malware and ransomware
- Behavior-based indicators of attack (IOAs) prevent sophisticated fileless and malware-free attacks
- Exploit blocking stops the execution and spread of threats via unpatched vulnerabilities
- Threat intelligence prevention blocks activities known to be malicious
- Automated IOA remediation cleans up known artifacts left behind from blocked malicious activity
Key Product Capability

AI-POWERED NGAV
INTELLIGENT EDR
24/7 MANAGED THREAT HUNTING
AI-POWERED NGAV
- Protects against the entire spectrum without requiring daily update
- Combines the bestprevention technologies — machine learning, AI, indicators of attack (IOAs), exploit blocking and more — to stop ransomware and malware-free and fileless attacks
- Covers the gaps leftby legacy AV and fully protects endpoints online and offline
INTELLIGENT EDR
- Prevents silent failure bycapturing raw events for automatic detection ofmalicious activity, providing unparalleled visibility, proactive threat hunting and forensic investigation
- Unravels an entire attack in the easy-to-use CrowdScore™ Incident Workbench,enriched with context and threat intelligence dat
- Provides powerful response action to contain, investigate and remediate compromised systems
24/7 MANAGED THREAT HUNTING
- An elite team of security experts proactively hunts, investigates and adviseson activity in your environment to ensure threats and high-priority alerts don’t get missed
- Alert prioritization uniquely pinpoints the most urgentthreats in your environmentand resolves false positives
- Guided response provides clarity on an attack, showing you what to do next
DEVICE CONTROL
FIREWALL MANAGEMENT
THREAT INTELLIGENCE
DEVICE CONTROL
- Provides detailed visibility on USB device usage
- Enables granular policy enforcement to ensure control over USB devices used in the environment
FIREWALL MANAGEMENT
- Makes it easy to create, manage and enforce policies
- Defends against network threats and provides instant visibility to enhance protection and inform action
THREAT INTELLIGENCE
- Enables you to fully understand the threats in your environment and easily prioritize responses with threat severity assessment
- Eliminates guesswork so you can respond to threats decisively
- Automatically determines the scope and impact of threats found in your environment
- Provides a broader set of indicators of compromise (IOCs) for faster, better protection
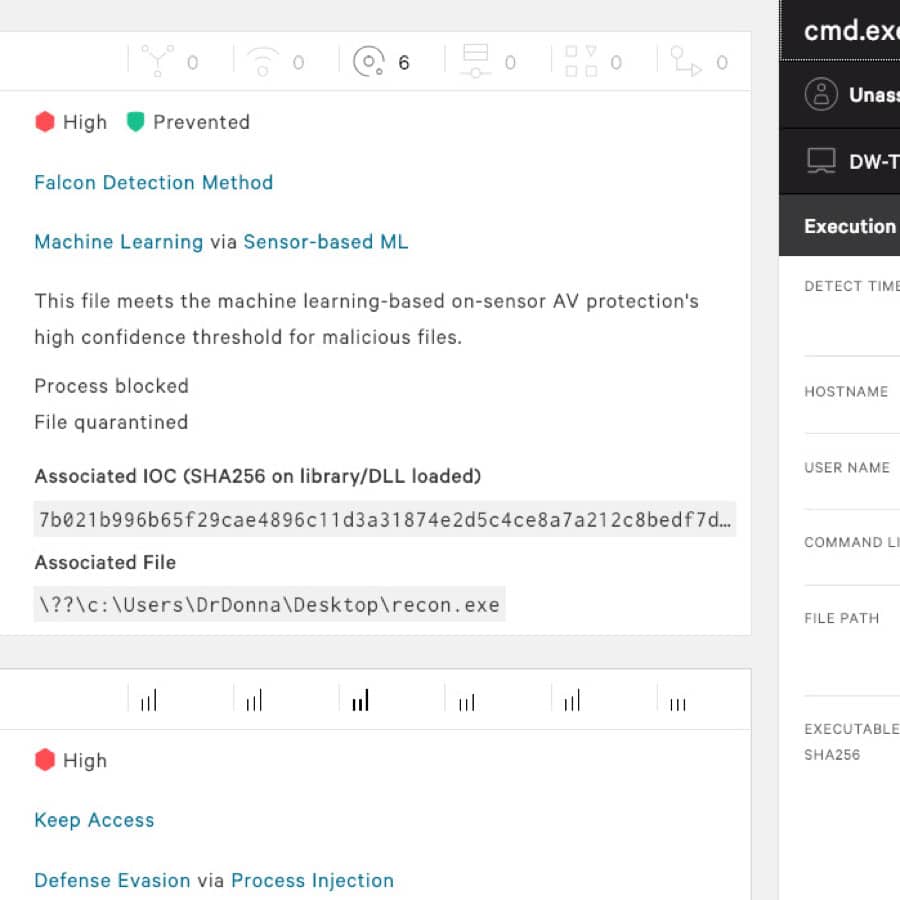
ScreenShot :
Previous
Next
Contact :
Email : sales@networks365.net
Line ID: @network365
Phone : 02-049-4059 , 081-657-0932